Writing this article takes me back to my first IT job out of college. I worked at a small ISP that also hosted email, web servers, backups, and other MSP services (before we called them MSPs). They days where my on-call included helping old ladies try different modem strings to get better dial-up connections (big shout out to https://www.modemhelp.net/ which is surprisingly still around!). I was also one of the help desk techs with the responsibility of helping users figure out why their emails weren’t being received or why they were getting bounce messages. A large majority of these resulted in us contacting organizations that hosted their own exchange servers. The majority were on blacklists for sending spam, had misconfigured MX or SPF records, or a myriad of other issues that came with hosting your own email server (yay open relays!).
That was back in the day of no real cloud solutions. Now we’re faced with an almost endless application that we can use for our email service. Understandably it was difficult for most admin’s to decide to switch to cloud hosting of email. Many because of the loss of control and sometimes functionality. Over the last few years we’ve started to take a turn into not having much of a choice. The reduced effort and increased security potential make it that much more appealing.
History of Exchange
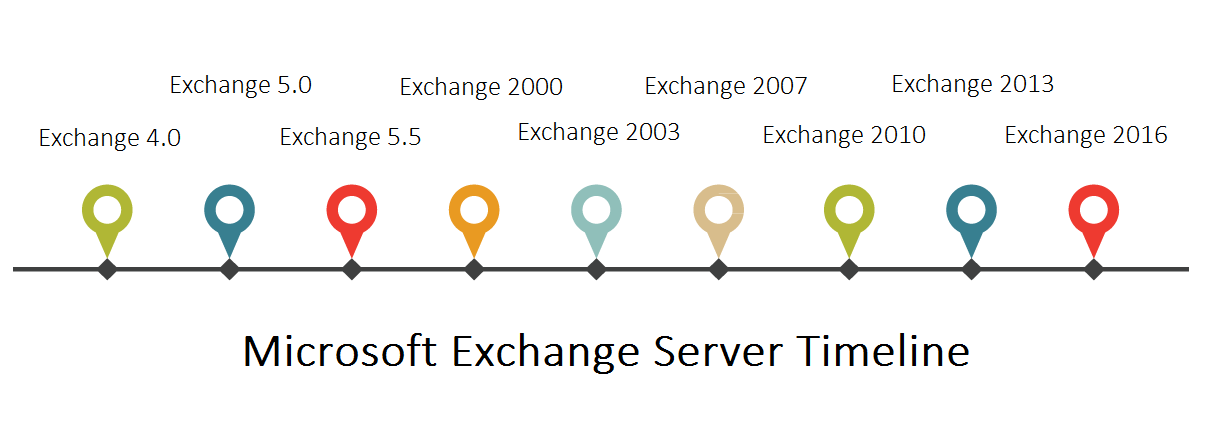
Microsoft Exchange Server was first released in 1996 as a messaging and collaborative software system that runs on Windows Server. The initial version focused on replacing earlier Microsoft messaging products like Schedule+ and Exchange Server 4.0. Major new versions followed with Exchange 2000 all the way to Exchange Server 2019. These updated versions introduced new features like better web access, mobile device synchronization, higher availability with database availability groups, and better integration with other Microsoft products and cloud services. While Microsoft will continue supporting Exchange Server 2019, until 2025, the focus has shifted to Exchange Online. The long-term outlook for on-premises Exchange is uncertain with Microsoft heavily investing in cloud offerings instead.
History of Exchange Online and MS365
Microsoft first introduced Exchange Online in 2008 as part of its new Software + Services strategy to offer hosted messaging and collaboration services in the cloud. After several years of slow growth, adoption of Exchange Online accelerated with the launch of Office 365 in 2011 which bundled Exchange Online with other cloud-based Office apps and services. Major updates since 2011 have added improved user interfaces, additional security and compliance capabilities, and closer integration with products like SharePoint Online, Teams, and Microsoft 365 apps.
Around 2020, Microsoft began advising all customers, including those currently using on-prem Exchange Server, to transition fully to Exchange Online for lower costs and improved productivity. Exchange Online now has advanced capabilities including 100 GB mailboxes, 1.5TB archiving, built-in malware and spam filtering, legal and in-place holds, and analytics from the Microsoft Graph. The number of organizations using Exchange Online has grown rapidly, with Microsoft reporting over 200 million monthly active commercial users by late 2022.
Breaches and Vulnerabilities
Having seen first hand many SMBs fall victim to On-Prem Exchange attacks over the last few years, one of my normal recommendations is to do your best to move to MS365. Not only will you not have to worry about the physical administration of it, you’ll see significantly less spam and direct attacks to your network. Even prior to upgrading you can follow steps to secure the Exchange you have.

Vulnerabilities
Some of the most impactful Exchange Server vulnerabilities over the past few years include:
- JET Database Flaw (2019-2020) – Two separate vulnerabilities were discovered over a year apart allowing remote code execution via Exchange’s JET database engine. Both had public exploits.
- Zerologon Vulnerability (2020) – Zerologon let attackers exploit a cryptographic flaw in Netlogon authentication on domain controllers, enabling admin access domain privileges. Exchange servers were one of the key targets.
- PrivExchange Vulnerability (2021) – This vulnerability allowed attackers to gain unauthorized access to private email content from Exchange on-prem systems. It did not require authentication, making it an easy target.
- ProxyShell Vulnerabilities (2021) – Disclosed shortly after ProxyLogon, ProxyShell was another set of three vulnerabilities that also enabled remote takeover of Exchange Servers. This compounded the problem for companies who had not yet patched systems.
- ProxyLogon Vulnerabilities (2021) – A set of four zero-day exploits collectively dubbed “ProxyLogon” allowed remote code execution and full admin access to Exchange Servers. These were extremely widespread attacks that impacted over 250,000 organizations globally.
Overall, the sheer prevalence of Exchange servers, handling sensitive email data, makes them a very attractive target for cyber attackers. Addressing vulnerabilities quickly via patches, upgrading legacy versions, and enhancing security controls are key to reducing overall risk exposure. The recent ProxyLogon and ProxyShell vulnerabilities truly demonstrated how a single exploit can lead to a global crisis scenario very rapidly across countless Exchange customers. Removing the ability for an attacker to move laterally in an environment is one of the largest advantages. If there is no way to establish a foothold to move through a network and compromise more data and more machines, you’ve limited the available scope of the attack. These threats demonstrate the growing security risks of managing on-premises Exchange servers and the protections gained through a cloud-based service like Exchange Online.
Common Process and Timelines
You might wonder what it takes to get from on-premises Exchange to Exchange Online in Microsoft 365. Just like most of what we do in tech, it depends greatly on how you plan and prepare for a move like this with how smooth it goes. Even well prepared technically you’ll still need a bit of end user training. With the increase of webmail as a service for home users over the last decade, hopefully it won’t be too much of a learning curve. Here is a common process and some best practices for migration.
Prepare
- In your on-prem environment ensure Exchange Server is on the latest supported version
- Enable hybrid configuration features
- Sync passwords to Azure AD using Azure AD Connect.
- Set up your Microsoft 365 tenant
- Add and verify domains, set security and compliance policies, enable auditing and alerts
Configure
- Install Microsoft 365 Hybrid Configuration wizard
- This will guide you through the activation and setup of a hybrid deployment with your on-prem Exchange org
- Configure Azure AD Connect for synchronization
- Synchronize user accounts, groups, and contacts from your on-prem AD to Office 365 Azure AD
Deploy
- Move mailboxes to Exchange Online
- Use batch migrations working set by set and migrate in test sets first. Validate moved mailboxes before moving more.
- Migrate public folders
- Decide to migrate with Hybrid or cutover migration. Validate folder structures, permissions, and hybrid functionality often.
- Establish coexistence and redirect traffic.
- Update your DNS records, configure an Exchange hybrid to route mail between environments.
- Send updates to users as you progress through migration stages.
Decommission
- Once fully migrated, remove any leftover mailboxes and objects, uninstall Exchange.
The average timeline to fully migrate can vary greatly depending on the size and complexity of an organization’s environment. Some general timelines are:
- Small business (<150 employees): Can often migrate in less than 1 month
- Mid-size company (150 – 1,000 employees): 3-6 months
- Large enterprise (>1,000 employees): 6-12 months
- Complex enterprise (10,000+ employees): 12-18+ months
Key factors that can shorten or extend timelines include:
- Number of mailboxes to migrate
- Network bandwidth limitations
- Complexity of folder structures and permissions
- Custom apps relying on legacy Exchange
- Priority of coexistence before decommissioning
- Whether migrating in phases vs. all at once
Building contingencies into timelines and leveraging Microsoft or third-party professional services can help ensure a successful migration within business requirements.
Conclusion
Given tighter IT budgets, shortage of skills and time to maintain on-prem infrastructure, and regulatory compliance demands, continuing to host Exchange servers lacks justification for many companies. Ultimately, the move to the cloud offers significant advantages. These include enhanced security features, reduced administrative overhead, better scalability, and continued innovation and support. As the world increasingly adopts cloud services, this migration is not just a trend but a strategic necessity. It’s important to ensure organizations stay agile, secure, and competitive in a rapidly evolving digital landscape.
Amanda Berlin
Amanda Berlin is the Senior Product Manager of Cybersecurity at Blumira, bringing nearly two decades of experience to her position. At Blumira she leads a team of incident detection engineers who are responsible for creating new detections based on threat intelligence and research for the Blumira platform. An...
More from the blog
View All Posts
Blumira Launches New Microsoft 365 Threat Response Feature for Faster and More Efficient Security Operations
Read More
Now Available: Microsoft 365 Threat Response From Blumira
Read More
Customer Story: District of Sparwood
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.