- Product
Product Overview
Sophisticated security with unmatched simplicityCloud SIEM
Pre-configured detections across your environmentHoneypots
Deception technology to detect lateral movementEndpoint Visibility
Real-time monitoring with added detection & responseSecurity Reports
Data visualizations, compliance reports, and executive summariesAutomated Response
Detect, prioritize, and neutralize threats around the clockIntegrations
Cloud, on-prem, and open API connectionsXDR Platform
A complete view to identify risk, and things operational
- Pricing
- Why Blumira
Why Blumira
The Security Operations platform IT teams loveWatch A Demo
See Blumira in action and how it builds operational resilienceUse Cases
A unified security solution for every challengePricing
Unlimited data and predictable pricing structureCompany
Our human-centered approach to cybersecurityCompare Blumira
Find out how Blumira stacks up to similar security toolsIntegrations
Cloud, on-prem, and open API connectionsCustomer Stories
Learn how others like you found success with Blumira
- Solutions
- Partners
- Resources
Ransomware Prevention & Detection
Detect threats 5X faster with Blumira’s advanced threat detection and response.
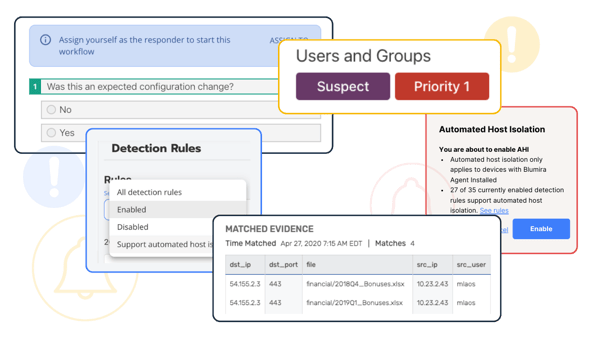
Ransomware Today
Once infected, ransomware can lock out users and/or encrypt an organization’s files. Cybercriminals will demand ransom in exchange for regaining access.
Ransomware is expected to grow to a $20 billion market by 2021, showing no signs of slowing down. Ransomware attacks increased 50% on a daily average over the last three months of 2021 (Cybersecurity Ventures | Check Point).
Blumira can help your organization prevent, detect and respond to attacks before they result in ransomware infection.
Detection at Every Stage of the Attack Lifecycle
Blumira is with you at every step of an attack.
-
Attack Stage: Discovery
Detect & Respond to Recon Scanning
Scanning is one way attackers perform reconnaissance on your network, seeking vulnerable areas to attack – a tactic used in the discovery stage of attack, according to MITRE’s ATT&CK framework. By detecting source IPs running port scanning tools on your network, Blumira can detect and alert you in the early stages of an attack, before ransomware infection.
-
Attack Stage: Credential Access
Detect & Respond to Access Attacks
RDP is the most common ransomware attack vector (Coveware). By brute-forcing or buying stolen RDP (Remote Desktop Protocol) credentials, an attacker can gain access to and infect your network with ransomware. Password spraying is another brute-force method used to gain initial access. Blumira can detect password spraying, account lockouts, RDP connections, open ports and more.
Blumira also provides security playbooks to guide you through best security practices and next steps. Practices like updating your firewall policies to block inbound connections from the internet help reduce your overall attack surface. -
Attack Stage: Privilege Escalation
Detect & Respond to New Admin Accounts
Once they’ve gained a foothold, attackers will often change privileges on user accounts in order to move laterally throughout your environment, as well as get permissions to install ransomware on your systems.
Blumira can detect and alert you whenever administrator-level accounts are added, and provide your IT or security team with guidance on how to mitigate the risk of privilege escalation. -
Attack Stage: Exfiltration
Detect & Respond to Data Exfiltration
While detecting stolen data leaving your environment often seems like the aftermath of a ransomware infection, attackers are now stealing data before infection to use as additional leverage for demanding a ransom. To prevent data exposure, Blumira detects data exfiltration via generic network protocols to alert you to an attacker’s actions. Blumira also detects any anomalous internal web traffic that can indicate an attempt to exfiltrate data out of your environment.
-
Attack Stage: Execution
Detect & Respond to Malicious Applications & Files
Attackers download and execute malicious files in order to install ransomware on your systems. By detecting when an application is dropping a new file or script onto a machine, Blumira notifies your team of potentially malicious executables that may not be allowlisted, and could present a threat to your organization. This visibility allows you to detect a ransomware attack early and respond quickly to block or contain it.
Detect & Respond to Recon Scanning
Scanning is one way attackers perform reconnaissance on your network, seeking vulnerable areas to attack – a tactic used in the discovery stage of attack, according to MITRE’s ATT&CK framework. By detecting source IPs running port scanning tools on your network, Blumira can detect and alert you in the early stages of an attack, before ransomware infection.
Detect & Respond to Access Attacks
RDP is the most common ransomware attack vector (Coveware). By brute-forcing or buying stolen RDP (Remote Desktop Protocol) credentials, an attacker can gain access to and infect your network with ransomware. Password spraying is another brute-force method used to gain initial access. Blumira can detect password spraying, account lockouts, RDP connections, open ports and more.
Blumira also provides security playbooks to guide you through best security practices and next steps. Practices like updating your firewall policies to block inbound connections from the internet help reduce your overall attack surface.
Detect & Respond to New Admin Accounts
Once they’ve gained a foothold, attackers will often change privileges on user accounts in order to move laterally throughout your environment, as well as get permissions to install ransomware on your systems.
Blumira can detect and alert you whenever administrator-level accounts are added, and provide your IT or security team with guidance on how to mitigate the risk of privilege escalation.
Detect & Respond to Data Exfiltration
While detecting stolen data leaving your environment often seems like the aftermath of a ransomware infection, attackers are now stealing data before infection to use as additional leverage for demanding a ransom. To prevent data exposure, Blumira detects data exfiltration via generic network protocols to alert you to an attacker’s actions. Blumira also detects any anomalous internal web traffic that can indicate an attempt to exfiltrate data out of your environment.
Detect & Respond to Malicious Applications & Files
Attackers download and execute malicious files in order to install ransomware on your systems. By detecting when an application is dropping a new file or script onto a machine, Blumira notifies your team of potentially malicious executables that may not be allowlisted, and could present a threat to your organization. This visibility allows you to detect a ransomware attack early and respond quickly to block or contain it.
See What Blumira Customers Are Saying
Hear from our clients directly.
“Y'all are better than Crowdstrike, you guys will detect something and Crowdstrike will just sit there costing me money.”
John Osburn
Owner, Compteca MSP
“Being able to send logs from clients, servers, network equipment and cloud sources is very important. Knowing what is going on at all times and being alerted to something occurring allows us to look into who did what, when, and find out what was going on which triggered the alert and allows us to respond very quickly.”
Khan H.
Network Engineer, Mid-size Transportation Company
“I received a Suspect indicator [Finding], and I appreciate how clean and easy to follow the analysis is. I am sold on Blumira’s ease of use and capabilities.”
Amitaf DaSilva
Principal, CompuNET Consulting LLC
Ransomware Prevention Resources
Resources to help you
Security Alerts
8 min read
| October 9, 2025
MySonicWall Cloud Backup Service Breach Leads to Exposed Configuration Files
Read More
Security Alerts
9 min read
| September 26, 2025
Cisco SNMP Zero-Day Vulnerability: Critical Patch and Mitigations
Read More
Security Trends and Info
15 min read
| July 25, 2025
Why “Silent But Deadly” Infostealers Are Summer’s Hottest Trend
Read More