Microsoft 365 Security Monitoring
Simplify security by improving your Microsoft 365 cloud security with detection, response, and reporting in one easy-to-use platform.
Free Microsoft 365 Cloud Security
Traditional SIEMs can take months to get fully operational. That’s why we designed the Blumira SIEM platform so any IT team can get out-of-the-box detection and response in minutes. With the Blumira Free edition you get:
How Blumira Detects M365 Common Attacks
See how Blumira stops these common attacks before they begin.
-
User & Access Security
Monitor Microsoft 365 Login Activity
Attackers may attempt to take over legitimate user accounts in your Microsoft 365 environment to gain initial access or move around laterally. Blumira detects:
-
Whenever multi-factor authentication (MFA) is disabled for an Azure Active Directory (AD) user
-
Anomalous access attempts or the creation or deletion of an application password
-
Any time a user clicks on a malicious URL or is restricted from sending an email
-
Any impossible travel activity, indicating unauthorized access
-
Multiple failed user logon attempts
- Critical events, notifying you to lock out compromised users and revoke sessions, directly within Blumira
-
-
Detect Privilege Escalation
Detect Privilege Escalation
Easily detect when Microsoft Exchange administrator privileges are elevated, which could indicate an attacker is attempting to gain additional permissions within your environment. Blumira identifies and sends you playbooks to respond to:
-
Privilege escalation
-
Creation of forwarding and redirect rules
-
Suspicious inbox rule creation
Attackers may use inbox rules to remove or delete emails in order to lengthen the amount of time before a compromise is detected.
-
-
Stop Data Exfiltration
Stop Data Exfiltration
Secure your data by detecting signs that an attacker or malicious insider is stealing your organization’s information. Blumira identifies:
-
When files are shared with personal email addresses
-
Mass file downloads
-
Whenever an email send limit is exceeded. This will protect against spam campaigns
-
-
Track Ransomware Activity
Malware & Ransomware Indicators
By detecting indicators of malware and ransomware early, Blumira helps your organization act quickly to minimize impact. Get alerted to:
-
High rate of file uploads or deletion activity that could indicate an adverse encryption process
-
Malware campaigns detected in SharePoint and OneDrive
-
Malware campaigns detected after mailbox delivery
-
Failed zero-hour auto purge when Microsoft’s email protection features are disabled
-
-
Identify Unusual Microsoft 365 Activity
Identify Unusual Microsoft 365 Activity
Blumira tracks anomalous activity in your environment:
-
Any activity from anonymous or suspicious IP addresses
-
Activity from infrequent countries or terminated users
-
Unusual external file behavior
-
Increases in phishing emails or ISPs (internet service providers) for an OAuth application
-
Suspicious email sending patterns
-
-
Reports & Summary Dashboard
Dig Deeper With Microsoft 365 Security Reports
With the Blumira free Microsoft SIEM solution, you can gain greater insight into security trends over time with basic reporting on:
- Disabled accounts, deleted contacts, and any group changes
- Password changes or resets, and user or device added
- Failed user login attempts, overall login reports, and logins outside of North America
- Impossible travel activity and successful logins outside of the U.S.
- SharePoint files previewed or accessed
Upgrade to any paid edition for advanced reporting features, including the ability to schedule reports to run periodically.
Monitor Microsoft 365 Login Activity
Attackers may attempt to take over legitimate user accounts in your Microsoft 365 environment to gain initial access or move around laterally. Blumira detects:
-
Whenever multi-factor authentication (MFA) is disabled for an Azure Active Directory (AD) user
-
Anomalous access attempts or the creation or deletion of an application password
-
Any time a user clicks on a malicious URL or is restricted from sending an email
-
Any impossible travel activity, indicating unauthorized access
-
Multiple failed user logon attempts
- Critical events, notifying you to lock out compromised users and revoke sessions, directly within Blumira
Detect Privilege Escalation
Easily detect when Microsoft Exchange administrator privileges are elevated, which could indicate an attacker is attempting to gain additional permissions within your environment. Blumira identifies and sends you playbooks to respond to:
-
Privilege escalation
-
Creation of forwarding and redirect rules
-
Suspicious inbox rule creation
Attackers may use inbox rules to remove or delete emails in order to lengthen the amount of time before a compromise is detected.
Stop Data Exfiltration
Secure your data by detecting signs that an attacker or malicious insider is stealing your organization’s information. Blumira identifies:
-
When files are shared with personal email addresses
-
Mass file downloads
-
Whenever an email send limit is exceeded. This will protect against spam campaigns
Malware & Ransomware Indicators
By detecting indicators of malware and ransomware early, Blumira helps your organization act quickly to minimize impact. Get alerted to:
-
High rate of file uploads or deletion activity that could indicate an adverse encryption process
-
Malware campaigns detected in SharePoint and OneDrive
-
Malware campaigns detected after mailbox delivery
-
Failed zero-hour auto purge when Microsoft’s email protection features are disabled
Identify Unusual Microsoft 365 Activity
Blumira tracks anomalous activity in your environment:
-
Any activity from anonymous or suspicious IP addresses
-
Activity from infrequent countries or terminated users
-
Unusual external file behavior
-
Increases in phishing emails or ISPs (internet service providers) for an OAuth application
-
Suspicious email sending patterns
Dig Deeper With Microsoft 365 Security Reports
With the Blumira free Microsoft SIEM solution, you can gain greater insight into security trends over time with basic reporting on:
- Disabled accounts, deleted contacts, and any group changes
- Password changes or resets, and user or device added
- Failed user login attempts, overall login reports, and logins outside of North America
- Impossible travel activity and successful logins outside of the U.S.
- SharePoint files previewed or accessed
Upgrade to any paid edition for advanced reporting features, including the ability to schedule reports to run periodically.
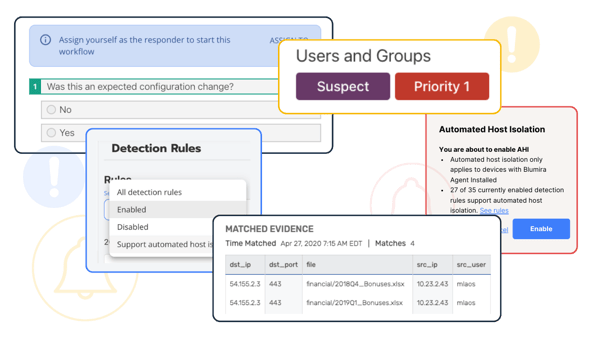
Unlock Greater Security Support & Coverage
It’s easy to upgrade to a paid edition including SIEM Pro, SIEM +, and XDR for:
-
24/7 Support – Blumira’s security operations team is available to help with urgent priority issues, onboarding, and guided response
-
Endpoint Visibility - Identify and prioritize endpoint risks, reduce your attack surface and prevent data loss with Blumira Agent.
-
Expanded Coverage – Gain broader visibility across your entire environment with additional cloud and on-premises third-party integrations
-
Automated Response – Block threats immediately with automatic host isolation, dynamic blocklists, and response actions directly within Blumira for faster remediation.
-
Extended Data Retention – Get one year of on-demand access to log data, ideal for compliance and cybersecurity insurance
Helping IT Teams Protect Their Microsoft Environment
Hear what our customers are saying.
“I researched a number of SIEM providers online and found most were way out-of-the-ballpark expensive, required a lot of infrastructure and didn’t provide a great return on our investment.”
Fritz Ludemann
Information Systems Administrator The City of Crescent City
“ Blumira added a new detection for malicious PowerShell activity. It flagged some activity in our environment. Blumira’s SecOps team immediately jumped on, saw that the scripts were legitimate activity coming from the Microsoft System Center monitoring agents, notified us that the alert was a false positive and that they had updated the detection rules for us.”
Matt Varblow
VP of Engineering Services, AdvantageCS
“ For a certain size of customer with no staff or only one security staff member, Blumira is an absolute godsend.”
Jason Waits
CISO, Inductive Automotive
Additional Resources for Microsoft 365 Cloud Monitoring
View More
Blumira Launches New Microsoft 365 Threat Response Feature for Faster and More Efficient Security Operations
Read More
Now Available: Microsoft 365 Threat Response From Blumira
Read More
Customer Story: District of Sparwood
Read MoreGet Started for Free
Experience the Blumira Free SIEM, with automated detection and response and compliance reports for 3 cloud connectors, forever.