Over 60% of organizations were victims of an email compromise attack in Q3 of 2021 (Abnormal Security). Attacks rose over 671% in June 2021, with threat actors targeting 33% of all organizations with brute-force attacks (seen below).
Microsoft is the top three of brands impersonated in BEC attacks, accounting for over 300 attacks seen that quarter.
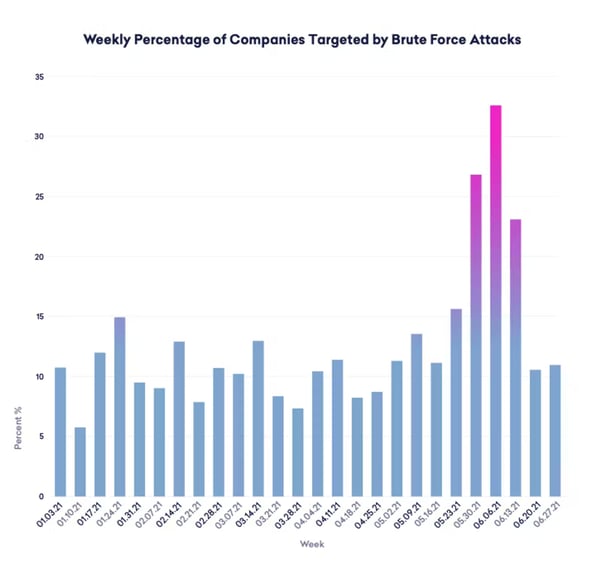
With the spike in business email compromise attacks, Blumira’s incident detection engineers have created, tested and automatically deployed detections to Blumira’s platform to help protect our customers from account compromise.
What is Business Email Compromise (BEC)?
Business email compromise (BEC) is when a threat actor uses social engineering (gathering info from social media sites) and impersonation to trick employees into sending payments or sensitive data to their accounts. These spoofed emails can lead to data theft, data breaches, movement to higher level employees, or the threat actor may hold on to the confidential information for future attacks.
One example is the impersonation of an executive, sending a spear phishing email to an employee asking for gift cards or wire transfers. With a legitimate-looking domain name or compromised employee’s email account, a recipient may be fooled into fulfilling the request out of a sense of urgency. BEC is basically a form of phishing attack that involves sending money directly to fraudulent accounts.
Email Security Trends: Scams Targeting SMBs & Cloud-Based Email
In an analysis of organizations by size, Abnormal Security researchers found that small to mid-sized companies were 43% more likely to experience a successful account takeover in that same quarter, potentially due to the fact that larger companies often have additional cybersecurity measures in place to help protect against brute-force cyberattacks.
Over the last decade, as organizations moved from on-site email systems to cloud-based, scammers have adapted. The FBI reports more than $2.1 billion in losses from cloud-based BEC scams between 2014 and 2019, with small and medium-sized businesses (SMBs) as the most vulnerable to these types of scams due to lack of resources and being priced out of most defensive security services.
How to Protect Against BEC Attacks
As in any attack, there are several different paths a cybercriminal may take to carry out a BEC scam. Below, you can see which methods are used, and what you should look for in your environment to detect and contain an attack in progress.

Potential signs of a BEC attack include phishing emails, spoofing, disabling of multi-factor authentication (MFA) protection on email account logins, inbox rule configurations or changes that allow for deleting email messages, enabling forwarding to external addresses and more.
It’s also important to have security awareness training for BEC attacks, so employees learn to distinguish between legitimate email and these “fraudsters”.
New Microsoft 365 Detections: Protect Against BEC and Other Attacks
To save you the manual effort of monitoring your logs for BEC attacks and other types of attack methods, Blumira’s platform automates 24/7 detection and response for possible cyber threats. We do this by writing new rules, testing them and tuning them for noise before releasing them to our platform.
Our platform identifies attacker methods early so you can respond quickly using our playbooks that accompany every finding. See our latest Microsoft 365 detection rules available now that protect against business email compromise and other attacks:
MFA Disabled For an Azure AD User
Blumira detects whenever a user’s multi-factor authentication (MFA) has been disabled in your Azure AD portal. Without secondary authentication, attackers can much more easily access sensitive information and pivot to other areas and accounts. This type of security misconfiguration has resulted in many cases of business email compromise (BEC).
Blumira sends this finding along with a playbook to help you respond with further instructions on investigation, including modifying and viewing your MFA policy within the Microsoft Azure Portal, then either removing users or re-enabling MFA for greater protection.
Activity From Suspicious IP Addresses
This detection identifies that users were active from an IP address that Microsoft Threat Intelligence identified as risky. These IP addresses are involved in malicious activities, such as performing password spraying, Botnet command and control (C2), and may indicate a compromised account. This detection uses a machine learning algorithm that reduces false positives, such as mis-tagged IP addresses that are widely used throughout the organization.
Blumira provides recommendations on next steps, including either closing out the finding as a known issue, reporting the finding as a false positive, or further investigating the user for potential compromise.
Unusual External User File Activity
Threat actors may use a number of techniques to exfiltrate, or steal data from your network. Microsoft 365 generates an alert whenever an unusually large number of activities are performed on files in SharePoint or OneDrive, including activities such as accessing files, downloading files, and deleting files.
Ransomware Activity
Blumira’s platform notifies you of ransomware activity that has been detected by Microsoft Defender for Cloud Apps. For example, if Defender for Cloud Apps identifies a high rate of file uploads or file deletion activities, it could indicate an adverse encryption process, according to Microsoft. Learn more by viewing Microsoft documentation on protecting your organization against ransomware.
See our many other new Microsoft 365 detection rules, developed and tested by our incident detection engineers to reduce noisy alerts while surfacing actionable data to help you respond quickly:
- Mass download
- Multiple failed user logon attempts to an app
- Unusual increase in email reported as phish
- Tenant restricted from sending unprovisioned email
- Tenant restricted from sending email
- Suspicious email sending patterns detected
- Malware campaign detected after delivery
These are the latest Microsoft 365 detection rules added to our platform – see other rules added last month in New Detections Update: Microsoft 365 Security.
Microsoft 365 Detection and Response Made Easy
With Blumira, we’ve made it fast and easy to achieve advanced visibility, detection, response and reporting capabilities across your Microsoft 365 environment.
Blumira’s behavior-based detections focused on real attack patterns can help you catch threats that typical endpoint detection and response (EDR) tools may miss due to relying on signature-based detections alone.

Cloud Security in Minutes: With Blumira’s Cloud Connectors, you can set up a cloud SIEM in minutes with pre-tuned detection rules applied automatically to your integration; no additional infrastructure, agent or sensor required. Now available for Microsoft 365, Duo Security and AWS.
“The process of configuring the connector was straightforward – taking only 10 minutes or so.” — Naveed Khan, Ennovo Group (MSP)
Affordable and Accessible to SMBs: Traditional SIEMs have priced out small and medium-sized businesses, proving to be too complex to set up and get operational. Blumira’s cloud SIEM is affordably priced and built for IT teams of any size to easily use. Our teams take care of the parsing, detection rules, tuning, data correlation and more so you can get more security value out of our SIEM with minimal time and effort.
Broad Security Coverage: With many different integrations and detections across on-premises and cloud services, Blumira gives you deeper visibility into third-party applications and correlates data across your endpoint security, identity, cloud infrastructure, firewall and many other solution providers to quickly identify threats and help guide you through response.
Thu Pham
Thu has over 15 years of experience in the information security and technology industries. Prior to joining Blumira, she held both content and product marketing roles at Duo Security, leading go-to-market (GTM) and messaging for the portfolio solution Cisco Zero Trust. She holds a bachelor of science degree in...
More from the blog
View All Posts
Protect Microsoft 365 With Blumira’s Free Edition
Read More
8 Microsoft 365 Detections You Get Free with Blumira
Read More
Understand Microsoft 365 Impossible Travel Rules
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.
