- Product
Product Overview
Sophisticated security with unmatched simplicityCloud SIEM
Pre-configured detections across your environmentHoneypots
Deception technology to detect lateral movementEndpoint Visibility
Real-time monitoring with added detection & responseSecurity Reports
Data visualizations, compliance reports, and executive summariesAutomated Response
Detect, prioritize, and neutralize threats around the clockIntegrations
Cloud, on-prem, and open API connectionsXDR Platform
A complete view to identify risk, and things operational
- Pricing
- Why Blumira
Why Blumira
The Security Operations platform IT teams loveWatch A Demo
See Blumira in action and how it builds operational resilienceUse Cases
A unified security solution for every challengePricing
Unlimited data and predictable pricing structureCompany
Our human-centered approach to cybersecurityCompare Blumira
Find out how Blumira stacks up to similar security toolsIntegrations
Cloud, on-prem, and open API connectionsCustomer Stories
Learn how others like you found success with Blumira
- Solutions
- Partners
- Resources
MDR vs. SIEM + XDR
Evaluating security solutions to find the right fit?
Here’s why you may want to choose a SIEM + XDR platform over MDR services.
SIEM + XDR expands visibility beyond just the endpoint while automating the manual, time-consuming, and error-prone work that MDRs must rely on staff to do. SIEM + XDR results in faster, more effective detection and response, while meeting compliance & cyber insurance requirements for data retention.
The Problem With MDRs
MDR (Managed Detection and Response) services offer alert investigation, triaging, threat hunting, and incident remediation. The idea of outsourcing all of your security can be appealing, especially to organizations with limited time or teams. However, MDRs promise a lot with varying degrees of fulfillment.
MDR teams are often overworked and staffed with junior analysts who are spread thin supporting many different clients, which results in poor performance issues and a heavy reliance on human expertise and prioritization across clients. MDR visibility is also often limited to endpoints, which results in missing earlier signals from other data sources that go untracked.
“A lot of MDRs are agent-only, and don’t provide a network component; using only an agent to build context around incidents. Since I can integrate Blumira directly with firewalls, I was alerted to a hacker from Moldova who was conducting password-spraying attacks on a customer’s firewall. I was able to find the IP address and block the attacks completely.”
Aaron Cervasio
Detection Delay
Lack of Control
Lack of Logs & Visibility
The Myth of Fully-Outsourced Security
The Advantages of SIEM + XDR
The Advantages of SIEM + XDR
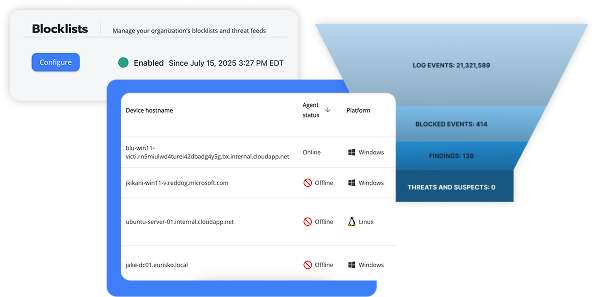
A SIEM (System Information and Event Management) solution provides a holistic view of your entire environment by collecting and normalizing data from your applications, systems, servers, endpoints, and more to provide continuous security monitoring. A SIEM should retain a complete history of your logs for compliance and cyber insurance.
When paired with XDR (Extended Detection and Response) capabilities, the solution can identify threats, triage events, prioritize findings, and provide both guided and automated response. Automating the manual work of an MDR team results in faster detection and more efficient operations.
Why choose Blumira’s SIEM + XDR platform over MDR services:
-
Fastest Threat Detection

Get notified within a minute of initial detection, with no delay or manual triaging required. Expedite your remediation times and get early breach prevention with auto-deployed detection rules that are updated weekly and focused on signs of attacker behavior that’s correlated across data from many different sources beyond the endpoint.
-
Automation Reduces Work

The average user spends less than 15 minutes a day managing Blumira. Save time spent on manual tasks, and eliminate the need to hire a security team with Blumira’s platform that automates 24/7 monitoring, detection, triaging, notifying, and providing steps for response — as well as automated endpoint isolation to contain threats immediately, no human intervention required.
-
Total Log Visibility & Retention

Gain direct access to your logs with the ability to search, export, and send automated reports, thanks to Blumira’s SIEM which retains a year of complete log history with unlimited data ingestion at a flat fee. Fully intact logs are critical to determine the scope of an incident, helping meet compliance and cyber insurance requirements for data retention.
-
24/7 Security Operations

In addition to an automated platform, you also have access to Blumira’s security team 24/7 to provide guided response, troubleshoot issues, and more when you have a critical issue. With a 99.7% customer satisfaction score and an average 18-minute response time, you can rest easy knowing you’re in good hands.

Get notified within a minute of initial detection, with no delay or manual triaging required. Expedite your remediation times and get early breach prevention with auto-deployed detection rules that are updated weekly and focused on signs of attacker behavior that’s correlated across data from many different sources beyond the endpoint.

The average user spends less than 15 minutes a day managing Blumira. Save time spent on manual tasks, and eliminate the need to hire a security team with Blumira’s platform that automates 24/7 monitoring, detection, triaging, notifying, and providing steps for response — as well as automated endpoint isolation to contain threats immediately, no human intervention required.

Gain direct access to your logs with the ability to search, export, and send automated reports, thanks to Blumira’s SIEM which retains a year of complete log history with unlimited data ingestion at a flat fee. Fully intact logs are critical to determine the scope of an incident, helping meet compliance and cyber insurance requirements for data retention.

In addition to an automated platform, you also have access to Blumira’s security team 24/7 to provide guided response, troubleshoot issues, and more when you have a critical issue. With a 99.7% customer satisfaction score and an average 18-minute response time, you can rest easy knowing you’re in good hands.
Since transitioning to the co-managed model and implementing Blumira, IT Manager Paul Silvestri estimates a 60% reduction in support requests.
Blumira’s Managed Detections and Proactive Outreach
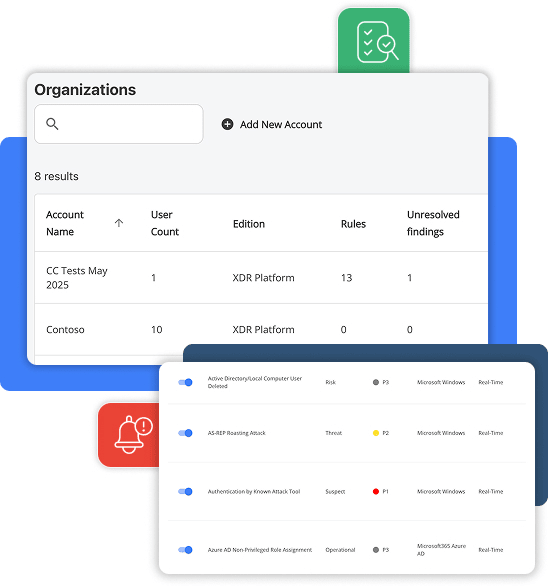
To help our customers identify indicators of compromise early and often, Blumira’s
incident detection team manages the detection rules that power our platform.
Tasks include:
Threat hunting & releasing new detections every week
Prioritizing detections for critical security vulnerabilities & exploits
Ensuring actionable findings are sent within minutes (or less) of initial detection
Proactive outreach to customers about malicious activity seen in their environment
Creating custom detections for customers
Assisting in incident response activities during a customer incident
Tuning detections to reduce false positives & noisy alerts
<
Discover the Blumira Difference
Dive into how Blumira simplifies cybersecurity for IT teams. From setup to real-world use cases, our demo covers everything you need to start your security transformation. No preparation needed, just curiosity.
Request A Demo
(*) Required Fields