Cybersecurity for Retail
Cybersecurity is an ongoing concern for retail organizations. The retail sector is also highly regulated by compliance frameworks such as PCI-DSS. In 2021, cyberattacks on retail and e-commerce organizations surged by 264%, according to a SonicWall report. One in every five ransomware attacks targeted a retail company.
Limited Resources Leave Retail Organizations At Risk
While many retail organizations turn to traditional Security Information and Event Management (SIEM) platforms to detect cybersecurity threats, most organizations have limited resources to engineer the product to work effectively.
Traditional SIEMs require regular optimization to defend against the latest cyberattacks. In large corporations, a 24/7 Security Operations Center (SOC) staffed by a group of specialized IT security analysts sift through alerts, determine the severity of each, take action on the most important ones, and feed and maintain the system on an ongoing basis.
Common Security Risks and Challenges for Retail Companies
Take a look at some of the most common risks and hurdles for the retail sector.
Cybersecurity Best Practices for Retail Companies
There are some best practices that IT teams in retail can follow, even with limited budgets and staff.
-
Prioritize end user training
Prioritize End User Training
IT and security teams should know about ransomware warning signs, but so should end users. Failure to train and educate users often points to a broader issue — a lack of security. That, combined with the fact that human error is the starting point for many cyberattacks, means that organizations should make training more of a priority.
At a minimum, IT and security teams should inform staff about how to spot a phishing email. More formal security awareness training is even better, but an informal chat about what a phishing email can look like and what to do is a good first step.
-
Deploy Sysmon
Deploy Sysmon
When it comes to preventing ransomware, it’s important to have visibility into an environment. Endpoint detection and response (EDR) tools can achieve that, but they can also be prohibitively expensive for retail establishments with limited budgets. System Monitor (Sysmon for short) is a free Microsoft utility that small IT teams can use to get visibility into their environments. Sysmon is part of the Sysinternals software package and provides a higher level of event monitoring than the standard Windows logs. It records events such as network connections, process creations, file hashes, and changes to the Windows Registry.
IT leaders without the budget for an EDR solution should deploy Sysmon for enhanced logging that can provide a wealth of data about endpoints. Since Sysmon is free, it does require more care and feeding than a plug-and-play paid tool. IT admins need to deploy updates as they are released and make configuration changes as necessary, but those tasks generally fall under the umbrella of standard patch management. It’s relatively easy to install and configure Sysmon in a few steps.
-
Implement Threat Detection and Response
Implement Threat Detection and Response
Using Sysmon and a centralized log management tool will provide some visibility into an environment and help with alerting, but small IT and security teams need to know how to respond to those alerts. A threat detection and response solution alerts IT and security teams on suspicious behavior that is indicative of a ransomware attack.
Prioritize End User Training
IT and security teams should know about ransomware warning signs, but so should end users. Failure to train and educate users often points to a broader issue — a lack of security. That, combined with the fact that human error is the starting point for many cyberattacks, means that organizations should make training more of a priority.
At a minimum, IT and security teams should inform staff about how to spot a phishing email. More formal security awareness training is even better, but an informal chat about what a phishing email can look like and what to do is a good first step.
Deploy Sysmon
When it comes to preventing ransomware, it’s important to have visibility into an environment. Endpoint detection and response (EDR) tools can achieve that, but they can also be prohibitively expensive for retail establishments with limited budgets. System Monitor (Sysmon for short) is a free Microsoft utility that small IT teams can use to get visibility into their environments. Sysmon is part of the Sysinternals software package and provides a higher level of event monitoring than the standard Windows logs. It records events such as network connections, process creations, file hashes, and changes to the Windows Registry.
IT leaders without the budget for an EDR solution should deploy Sysmon for enhanced logging that can provide a wealth of data about endpoints. Since Sysmon is free, it does require more care and feeding than a plug-and-play paid tool. IT admins need to deploy updates as they are released and make configuration changes as necessary, but those tasks generally fall under the umbrella of standard patch management. It’s relatively easy to install and configure Sysmon in a few steps.
Implement Threat Detection and Response
Using Sysmon and a centralized log management tool will provide some visibility into an environment and help with alerting, but small IT and security teams need to know how to respond to those alerts. A threat detection and response solution alerts IT and security teams on suspicious behavior that is indicative of a ransomware attack.

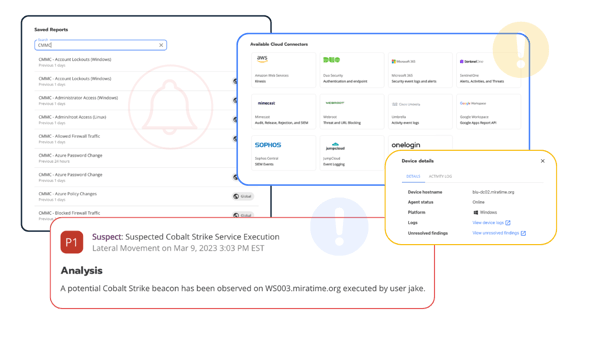
Blumira Addresses the Retail Cybersecurity Gap
Blumira is a PCI-compliant SIEM with threat detection and response that alerts your team about critical cyber threats in real-time and provides automated and actionable response capabilities that reduce the overhead associated with traditional SIEM products.
With Blumira Free SIEM edition, you can detect and respond to threats for 3 cloud integrations. It’s fast, easy, and free for IT and security teams in the retail industry to use.
Additional Cybersecurity Resources
View All
Customer Story: National Conference of Insurance Guaranty Funds
Read More
Blumira Briefings: Disclosure Drama, Ransomware Breakdown, and MFA Bypass Techniques
Read More
SIEM Starter: A Budget-Friendly SIEM That Meets Compliance & Keeps You Secure
Read MoreGet Started for Free
Experience the Blumira Free SIEM, with automated detection and response plus compliance reports for 3 cloud connectors, forever.