NIST CSF
Blumira’s security platform helps organizations easily meet and support multiple NIST CSF core functions and outcomes, including threat detection, security continuous monitoring, adverse event analysis, incident response reporting and communication, incident analysis, and more.
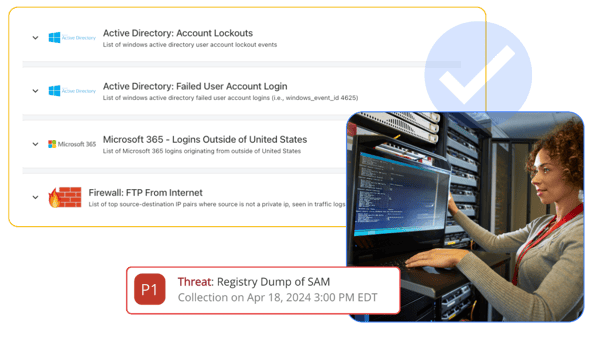
NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) 2.0 is designed to help organizations of all sizes and sectors — including industry, government, academia, and nonprofit — to manage and reduce their cybersecurity risks. Although not prescriptive, the CSF assists its users in learning about and selecting specific outcomes.
The CSF core functions organize cybersecurity outcomes at their highest level: Govern, Identify, Protect, Detect, Respond, and Recover.
- Govern: Cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
- Identify: Understand and manage cyber risks to systems, assets, data, and capabilities.
- Protect: Implement safeguards to prevent or limit the impact of cybersecurity incidents.
- Detect: Develop and implement capabilities to identify cybersecurity events promptly.
- Respond: Take appropriate actions to mitigate the impact of cybersecurity incidents.
- Recover: Restore affected systems, services, and capabilities to normal operations after a cybersecurity incident.
How Blumira Helps With DE: Detect
DE.CM: Security Continuous Monitoring
-
DE.CM-01: Networks and network services are monitored to find potentially adverse events
DE.CM-01:
Networks and network services are monitored to find potentially adverse events
Blumira automates the monitoring of an organization’s network and environment to help identify anomalies indicative of malicious acts and operational errors, analyzing them with detection rules designed to determine if they are a security event. Blumira has rules that identify potential use of compromised credentials, unauthorized access, connection of unauthorized software and more. -
DE.CM-03: Personnel activity and technology usage are monitored to find potentially adverse events
DE.CM-03:
Personnel activity and technology usage are monitored to find potentially adverse events
Blumira retains security event logs for up to one year. That gives you an audit trail to trace malicious activity back to specific users, with IP addresses, usernames, timestamps, and more to help your organization investigate any suspicious activity related to both internal and external threats. The Blumira platform monitors remote access attempts (through VPNs, two-factor authentication, etc.) and any anomalous user activity, such as data exfiltration or lockouts, that may be indicative of compromised accounts or attacker lateral movement. Blumira’s honeypots also provide deception technology to track unauthorized access attempts. -
DE.CM-06: External service provider activities and services are monitored to find potentially adverse events
DE.CM-06:
External service provider activities and services are monitored to find potentially adverse events
Blumira's platform integrates with a wide range of third-party applications, cloud infrastructure and service providers; collecting logs and analyzing them for potentially adverse events. These detection rules are written, tested, tuned and updated by incident detection engineers, looking for signs of attacker activity. Real-time alerts are sent to teams within minutes of initial detection with guidance on how to respond. Blumira’s platform provides 24/7 automated monitoring of third-party activity to protect against external and internal threats. -
DE.CM-09: Computing hardware and software, runtime environments, and their data are monitored to find potentially adverse events
DE.CM-09:
Computing hardware and software, runtime environments, and their data are monitored to find potentially adverse events
Blumira's platform integrates with applications, analyzing data and monitoring email, web, file-sharing, collaboration services and other common attack vectors to detect malware, phishing, data exfiltration, and other adverse events. Blumira monitors authentication attempts, identifying and notifying teams of attacks against credentials. Blumira detects indicators of malicious activity and malware, including ransomware, alerting teams within minutes of initial detection and providing guidance on how to respond. Blumira Agent monitors endpoints and performs automatic threat containment for affected devices, isolating them from the rest of the network to prevent the spread of malware until further investigation.
DE.CM-01:
Networks and network services are monitored to find potentially adverse events
Blumira automates the monitoring of an organization’s network and environment to help identify anomalies indicative of malicious acts and operational errors, analyzing them with detection rules designed to determine if they are a security event. Blumira has rules that identify potential use of compromised credentials, unauthorized access, connection of unauthorized software and more.DE.CM-03:
Personnel activity and technology usage are monitored to find potentially adverse events
Blumira retains security event logs for up to one year. That gives you an audit trail to trace malicious activity back to specific users, with IP addresses, usernames, timestamps, and more to help your organization investigate any suspicious activity related to both internal and external threats. The Blumira platform monitors remote access attempts (through VPNs, two-factor authentication, etc.) and any anomalous user activity, such as data exfiltration or lockouts, that may be indicative of compromised accounts or attacker lateral movement. Blumira’s honeypots also provide deception technology to track unauthorized access attempts.DE.CM-06:
External service provider activities and services are monitored to find potentially adverse events
Blumira's platform integrates with a wide range of third-party applications, cloud infrastructure and service providers; collecting logs and analyzing them for potentially adverse events. These detection rules are written, tested, tuned and updated by incident detection engineers, looking for signs of attacker activity. Real-time alerts are sent to teams within minutes of initial detection with guidance on how to respond. Blumira’s platform provides 24/7 automated monitoring of third-party activity to protect against external and internal threats.DE.CM-09:
Computing hardware and software, runtime environments, and their data are monitored to find potentially adverse events
Blumira's platform integrates with applications, analyzing data and monitoring email, web, file-sharing, collaboration services and other common attack vectors to detect malware, phishing, data exfiltration, and other adverse events. Blumira monitors authentication attempts, identifying and notifying teams of attacks against credentials. Blumira detects indicators of malicious activity and malware, including ransomware, alerting teams within minutes of initial detection and providing guidance on how to respond. Blumira Agent monitors endpoints and performs automatic threat containment for affected devices, isolating them from the rest of the network to prevent the spread of malware until further investigation.DE.AE: Adverse Event Analysis
-
DE.AE-02: Potentially adverse events are analyzed to better understand associated activities
DE.AE-02:
Potentially adverse events are analyzed to better understand associated activities
NIST's implementation example: Use security information and event management (SIEM) or other tools to continuously monitor log events for known malicious and suspicious activity. Blumira's SIEM platform provides continuous log monitoring, alerting you to known malicious and suspicious activity with guidance on how to respond. Blumira also leverages threat intelligence feeds to enhance detection of threat actors and indicators of compromise. Blumira's reporting tools can generate automatic and scheduled reports on these findings. -
DE.AE-03: Information is correlated from multiple sources
DE.AE-03:
Information is correlated from multiple sources
Blumira aggregates log data generated by sources in your environment to a centralized location. The SIEM platform correlates data collected from different sources, allowing you to search and easily find all data related to an incident. The platform integrates with threat intelligence feeds to identify known malicious events across log sources. -
DE.AE-04: The estimated impact and scope of adverse events are understood
DE.AE-04:
The estimated impact and scope of adverse events are understood
NIST's implementation example: Use SIEMs or other tools to estimate impact and scope, and review and refine the estimates. Blumira's SIEM platform comes with integrations and detection rules that automatically estimate and prioritize findings by criticality (or adverse events) to help organizations understand what needs immediate attention and response. Blumira Investigate can help organizations research impacted users, endpoints and more to determine the scope of an incident.
DE.AE-02:
Potentially adverse events are analyzed to better understand associated activities
NIST's implementation example: Use security information and event management (SIEM) or other tools to continuously monitor log events for known malicious and suspicious activity. Blumira's SIEM platform provides continuous log monitoring, alerting you to known malicious and suspicious activity with guidance on how to respond. Blumira also leverages threat intelligence feeds to enhance detection of threat actors and indicators of compromise. Blumira's reporting tools can generate automatic and scheduled reports on these findings.DE.AE-03:
Information is correlated from multiple sources
Blumira aggregates log data generated by sources in your environment to a centralized location. The SIEM platform correlates data collected from different sources, allowing you to search and easily find all data related to an incident. The platform integrates with threat intelligence feeds to identify known malicious events across log sources.DE.AE-04:
The estimated impact and scope of adverse events are understood
NIST's implementation example: Use SIEMs or other tools to estimate impact and scope, and review and refine the estimates. Blumira's SIEM platform comes with integrations and detection rules that automatically estimate and prioritize findings by criticality (or adverse events) to help organizations understand what needs immediate attention and response. Blumira Investigate can help organizations research impacted users, endpoints and more to determine the scope of an incident.-
DE.AE-06: Information on adverse events is provided to authorized staff and tools
DE.AE-06:
Information on adverse events is provided to authorized staff and tools
Blumira's platform generates alerts that are sent to teams of responders, with real-time notifications sent within minutes of initial detection of a security event. All log analysis findings can be accessed within the Blumira application, with a year of data retention available for review. -
DE.AE-07: Cyber threat intelligence and other contextual information are integrated into the analysis
DE.AE-07:
Cyber threat intelligence and other contextual information are integrated into the analysis
To help inform Blumira’s platform of new threats and relevant security information, Blumira ingests different types of data feeds. Those include threat feeds, information/risk feeds and safe feeds. With this data, analysts can enhance detections and enrich data to help reduce the time to identify, respond and contain potential threats. Blumira's detection rules identify and notify responders about known vulnerabilities, hacker tools, malicious traffic and more seen in their environment. Each finding sent to responders includes an integrated analysis and description of the identified security event, the potential impact on the organization, and other relevant contextual information to help them with threat response. -
DE.AE-08: Incidents are declared when adverse events meet the defined incident criteria
DE.AE-08:
Incidents are declared when adverse events meet the defined incident criteria
Blumira can help support organizations in determining if an incident should be declared by providing security guidance from Blumira’s Security Operations (SecOps) team, available 24/7 for critical priority issues. Blumira’s security team helps organizations understand when critical security events are occurring, and provides assistance to help prevent and support organizations during and after incidents.
DE.AE-06:
Information on adverse events is provided to authorized staff and tools
Blumira's platform generates alerts that are sent to teams of responders, with real-time notifications sent within minutes of initial detection of a security event. All log analysis findings can be accessed within the Blumira application, with a year of data retention available for review.DE.AE-07:
Cyber threat intelligence and other contextual information are integrated into the analysis
To help inform Blumira’s platform of new threats and relevant security information, Blumira ingests different types of data feeds. Those include threat feeds, information/risk feeds and safe feeds. With this data, analysts can enhance detections and enrich data to help reduce the time to identify, respond and contain potential threats. Blumira's detection rules identify and notify responders about known vulnerabilities, hacker tools, malicious traffic and more seen in their environment. Each finding sent to responders includes an integrated analysis and description of the identified security event, the potential impact on the organization, and other relevant contextual information to help them with threat response.DE.AE-08:
Incidents are declared when adverse events meet the defined incident criteria
Blumira can help support organizations in determining if an incident should be declared by providing security guidance from Blumira’s Security Operations (SecOps) team, available 24/7 for critical priority issues. Blumira’s security team helps organizations understand when critical security events are occurring, and provides assistance to help prevent and support organizations during and after incidents.RS: Respond
RS.AN: Incident Analysis
-
RS.AN-03: Analysis is performed to establish what has taken place during an incident and the root cause of the incident
RS.AN-03:
Analysis is performed to establish what has taken place during an incident and the root cause of the incident
Blumira provides an audit trail of events that occurred during incidents, giving organizations information about the assets and resources involved in each event. Blumira's findings also surface data about vulnerabilities and threat actor groups involved. Blumira Investigate can help teams analyze incidents to determine root cause and scope. -
RS.AN-06: Actions performed during an investigation are recorded, and the records’ integrity and provenance are preserved
RS.AN-06:
Actions performed during an investigation are recorded, and the records’ integrity and provenance are preserved
Blumira provides a complete audit trail of events that occurred during incidents, with measures taken to ensure the logs cannot be tampered with or altered. Data is encrypted in transit and at rest, and access to the database is only granted to users that require it to do their jobs (least privilege access). -
RS.AN-07: Incident data and metadata are collected, and their integrity and provenance are preserved
RS.AN-07:
Incident data and metadata are collected, and their integrity and provenance are preserved
Blumira’s platform gathers and correlates data across your environment (that’s configured for logging), then populates this data with every alert. That includes detailed information such as source, date, username, timestamp, source and destination addresses and more to help with forensic investigations. Additionally, Blumira’s reporting provides up to one year of log retention history available on-demand to assist with investigations. -
RS.AN-08: An incident’s magnitude is estimated and validated
RS.AN-08:
An incident’s magnitude is estimated and validated
Blumira provides an audit trail of events that occurred during incidents, giving organizations information about the assets and resources involved in each event. Blumira's findings also surface data about vulnerabilities and threat actor groups involved. Blumira Investigate can help teams analyze incidents to determine root cause, scope and if other assets are affected. Blumira Agent can automatically identify and isolate all affected devices to contain a threat immediately after detection, cutting off access to the network until further investigation.
RS.AN-03:
Analysis is performed to establish what has taken place during an incident and the root cause of the incident
Blumira provides an audit trail of events that occurred during incidents, giving organizations information about the assets and resources involved in each event. Blumira's findings also surface data about vulnerabilities and threat actor groups involved. Blumira Investigate can help teams analyze incidents to determine root cause and scope.RS.AN-06:
Actions performed during an investigation are recorded, and the records’ integrity and provenance are preserved
Blumira provides a complete audit trail of events that occurred during incidents, with measures taken to ensure the logs cannot be tampered with or altered. Data is encrypted in transit and at rest, and access to the database is only granted to users that require it to do their jobs (least privilege access).RS.AN-07:
Incident data and metadata are collected, and their integrity and provenance are preserved
Blumira’s platform gathers and correlates data across your environment (that’s configured for logging), then populates this data with every alert. That includes detailed information such as source, date, username, timestamp, source and destination addresses and more to help with forensic investigations. Additionally, Blumira’s reporting provides up to one year of log retention history available on-demand to assist with investigations.RS.AN-08:
An incident’s magnitude is estimated and validated
Blumira provides an audit trail of events that occurred during incidents, giving organizations information about the assets and resources involved in each event. Blumira's findings also surface data about vulnerabilities and threat actor groups involved. Blumira Investigate can help teams analyze incidents to determine root cause, scope and if other assets are affected. Blumira Agent can automatically identify and isolate all affected devices to contain a threat immediately after detection, cutting off access to the network until further investigation.RS.CO: Incident Response Reporting And Communication
-
RS.CO-03: Information is shared with designated internal and external stakeholders
RS.CO-03:
Information is shared with designated internal and external stakeholders
Blumira helps support information-sharing with stakeholders by providing findings with contextual information about an attacker's observed TTPs (Tactics, Techniques, and Procedures) along every stage of attack. Some examples of TTPs include Network Denial of Service (DoS) attacks, exfiltration over alternative protocols, supply chain compromise, compromised cloud account credentials, public-facing application exploits and more.
RS.CO-03:
Information is shared with designated internal and external stakeholders
Blumira helps support information-sharing with stakeholders by providing findings with contextual information about an attacker's observed TTPs (Tactics, Techniques, and Procedures) along every stage of attack. Some examples of TTPs include Network Denial of Service (DoS) attacks, exfiltration over alternative protocols, supply chain compromise, compromised cloud account credentials, public-facing application exploits and more.RS.MI: Incident Mitigation
-
RS.MI-01: Incidents are contained
RS.MI-01:
Incidents are contained
Blumira Agent monitors endpoints, identifies potentially adverse security events and threats, then automatically performs containment actions by isolating affected endpoints from the rest of the network until further investigation. Blumira's platform notifies responders to take action, and provides options for manual endpoint isolation, as well as configuring containment by priority level (P1-P3).
RS.MI-01:
Incidents are contained
Blumira Agent monitors endpoints, identifies potentially adverse security events and threats, then automatically performs containment actions by isolating affected endpoints from the rest of the network until further investigation. Blumira's platform notifies responders to take action, and provides options for manual endpoint isolation, as well as configuring containment by priority level (P1-P3).Additional Compliance Resources
View more
NIST Cybersecurity Framework Implementation for Mid-Market Companies: 2025 Update
Read MoreVideo - Security Monitoring Essentials for 2025 Compliance
Read MoreMeeting Florida's 2025 Cybersecurity Deadline: Funding and Compliance
Read MoreGet Started for Free
Experience the Blumira Free SIEM, with automated detection and response and compliance reports for 3 cloud connectors, forever.