- Product
Product Overview
Sophisticated security with unmatched simplicityCloud SIEM
Pre-configured detections across your environmentHoneypots
Deception technology to detect lateral movementEndpoint Visibility
Real-time monitoring with added detection & responseSecurity Reports
Data visualizations, compliance reports, and executive summariesAutomated Response
Detect, prioritize, and neutralize threats around the clockIntegrations
Cloud, on-prem, and open API connectionsXDR Platform
A complete view to identify risk, and things operational
- Pricing
- Why Blumira
Why Blumira
The Security Operations platform IT teams loveWatch A Demo
See Blumira in action and how it builds operational resilienceUse Cases
A unified security solution for every challengePricing
Unlimited data and predictable pricing structureCompany
Our human-centered approach to cybersecurityCompare Blumira
Find out how Blumira stacks up to similar security toolsIntegrations
Cloud, on-prem, and open API connectionsCustomer Stories
Learn how others like you found success with Blumira
- Solutions
- Partners
- Resources
Malicious scripts are a key part of every attack and pentest. These malicious scripts are often run in PowerShell (PS) within Windows environments. PowerShell is one of the most powerful tools available used to control a Windows machine from within. One of Blumira’s first recommendations for Windows environments is to only allow necessary users the ability to use PowerShell. The general end user should not have access to PowerShell in any way.
Oftentimes, PowerShell permissions are given to administrators, developers, security practitioners, and sometimes even third-parties that are issued credentials for access to the environment. Allowing these users to have access to PowerShell opens a security gap in your network. It allows for attackers to have an elevated foothold within your network as soon as they’re able to access one of those user accounts, hosts, or sessions.
What is Execution Policy Bypass?
When PowerShell isn’t appropriately locked down, running execution policy bypasses becomes quite easy to do. Windows calls the execution policy less of a safety feature, but more of a suggestion. As we know by now, attackers aren’t looking for domain admin suggestions when actively attempting to traverse through a network. This is where our detection team wanted to help. Although it’s not possible to audit every command user running in PowerShell from the Windows domain admin side, Blumira is able to detect on the scripts and commands using our robust command-line logging.
Here is what a bypass on the PowerShell command line looks like –
PowerShell.exe -ExecutionPolicy Bypass -File .runme.ps1
Just imagine .runme.ps1 gathers all current user information, passwords stored in plaintext, connections to shared drives, etc. This is how easy your execution policy is to bypass.
You may be asking yourself, “Why can’t I just ban the use of “Bypass” in PowerShell?” Unfortunately, you cannot prevent PowerShell from executing scripts, because that’s one of its main purposes. You can, however, set the policy to prevent scripts – or allow only signed scripts, for example, but anyone with access to run PowerShell.exe can use the ‘-ExecutionPolicy’ command line parameter to bypass your policy.
How Does Blumira Help?
Don’t worry though: Blumira has crafted a detection that will give you real-time alerts when ‘Bypass’ is used in your command line. All we need is for you to have command line logging setup with NXlog, one of our primary forms of Windows logging. That way, when you see one of our alerts trigger, you’ll see who was running the command, what command was run, and be able to review a few other helpful details. Your plan of action should be:
- Reach out to the user.
- Correlate the action with that user.
- If no correlation can be found, you should immediately lock the account in question.
- Start to mitigate a possible attack on your network.
Your Guide to Microsoft Security
To help organizations running Microsoft environments, our guide gives you practical, step-by-step Windows tips to significantly improve your visibility into malicious activity.
Nick Dixon
Nick is a cybersecurity professional with over a decade of experience in IT security and operations management. A Detroit native and graduate of Eastern Michigan University's Information Assurance program, he currently serves as Security Analysts & Technical Support Manager at Blumira, where he has advanced through...
More from the blog
View All Posts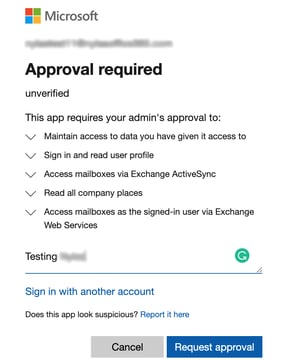
Blog
7 min read
| December 5, 2024
Protect Your Microsoft 365 Ecosystem from Third-Party App Risks
Read More
Security Alerts
10 min read
| May 26, 2020
Detecting RDP Attacks With Honeypots: Blumira Data Insights
Read More
Security How-To
4 min read
| March 23, 2021
Securing Cloud Infrastructure: Preventing Privilege Escalation in AWS
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.

