What Happened
French cybersecurity firm Olympe Cyberdefense discovered and disclosed a zero-day vulnerability in Fortinet (CVE-2022-40684) that enables unauthenticated remote code execution (RCE) on devices.
This security flaw affects devices running FortiOS SSL-VPN, according to Fortinet:
- FortiOS version 7.2.0 through 7.2.1
- FortiOS version 7.0.0 through 7.0.6
- FortiProxy version 7.2.0
- FortiProxy version 7.0.0 through 7.0.6
- FortiSwitchManager version 7.2.0
- FortiSwitchManager version 7.0.0
The bug is an authentication bypass vulnerability, which means that unauthenticated attackers are allowed to perform certain administrative tasks by means of specially-crafted HTTP or HTTPS requests. The most common administrative tasks performed by attackers are exfiltrating Fortinet device configurations and creating super admin accounts on the compromised device.
Fortinet quietly fixed the bug on November 28 with the release of FortiOS 7.2.3. On December 12, Fortinet released a security advisory FG-IR-22-398, warning that the vulnerability has been actively exploited in attacks. The advisory recommended customers to immediately validate their systems against indicators of compromise.
How Bad is This?
The vulnerability has a 9.8 score from National Vulnerability Database (NVD) and the CVE Numbering Authority (CNA), making it critical — the highest severity a vulnerability can receive.
An RCE is one of the most dangerous types of flaws because it allows an adversary to execute malicious code on vulnerable servers.
What Should I Do?
First, understand the scope and attack surface of your devices. Identify devices that are not updated to the fixed system versions.
Any device that was running a vulnerable version, and exposed to the Internet should be examined for signs of compromise. If an attacker leveraged this vulnerability to compromise your firewall, applying the patch is unlikely to remove the attacker’s ongoing access.
The best, and possibly only, way to detect if the firewall has been compromised is with the below indicators of compromise. If you are unsure if your firewall has been compromised, or if you have identified signs of compromise, engage with an incident response professional to determine next steps.
You’ll likely need to take the suspect firewall offline for the investigation process to happen. This will cause a service outage, but this step ensures that security is restored to your network.
If you carry cyber liability or similar types of insurance, you should immediately reach out to your insurer, as they may have resources to provide in the event of a suspected incident.
How To Detect
Once all affected devices have been identified, review their logs for indicators of compromise. If your logs are being stored in a SIEM or other separate log analysis system, you should be able to examine the logs in that way. Fortinet has shared the following indicators of compromise:
- Any log entry associated with the user “Local_Process_Access”
- Log entries with the message “System config file has been downloaded by user Local_Process_Access via {source}”
- Source has been seen as “Report Runner” or “Node.js”
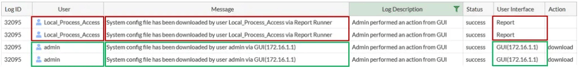
- Logs showing IOC will be located under the “System Events” subtype
How Blumira Can Help
Blumira’s incident detection engineering (IDE) team has created a detection in response to this vulnerability, called “Fortigate: Authentication Bypass CVE-2022-40684.” This enables customers to detect instances of CVE-2022-40684 being exploited in their environment.
Blumira’s cloud SIEM detects and alerts you about suspicious behavior in your environment so that you can stop an incident early enough to prevent damage. Each finding we send is accompanied with a security playbook, giving you clear recommendations on how to remediate an attack. Our support team of security analysts is always available to answer questions on how to interpret a finding, or for other security help.
For further technical details, see:
- https://www.truesec.com/hub/blog/fortinet-cve-2022-40684-vulnerability-from-an-incident-response-perspective
- https://www.fortiguard.com/psirt/FG-IR-22-377
- https://www.fortinet.com/blog/psirt-blogs/update-regarding-cve-2022-40684
- https://nvd.nist.gov/vuln/detail/CVE-2022-40684
Chris Furner, Senior Sales Engineer, contributed to this report.
Jake Ouellette
Jake is an Incident Detection Engineer at Blumira, where he contributes to research and design efforts to continuously improve the detection, analysis, and disruption capabilities of the Blumira platform.
More from the blog
View All Posts
New Unauthenticated Remote Code Execution Flaw Identified in OpenSSH Server
Read More
CVE-2024-3400: Palo Alto Vulnerabilities in GlobalProtect Gateway Lead to RCE
Read More
CVE-2024-3094: xz-utils (liblzma) Backdoor
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.
