Update – 5:45pm 2.21.24 – Detections have been built and tested and are in the process of being deployed to all of our customers. There are three new detections overall and all three are enabled by default:
- ConnectWise ScreenConnect Path Traversal Exploitation CVE-2024-1708
- Identifies IOC artifacts in C:\Program Files (x86)\ScreenConnect\App_Extensions\
- utilizes Windows EID 4663, Sysmon EID 11, or Blumira Agent
- ConnectWise ScreenConnect SetupWizard User Database Modification CVE-2024-1709
- Identifies IOC artifacts in C:\Windows\Temp\ScreenConnect
- utilizes Windows EID 4663, Sysmon EID 11, or Blumira Agent
- ConnectWise ScreenConnect SetupWizard Authentication Bypass CVE-2024-1709
- Identifies web requests made with to SetupWizard.aspx trailing path
- utilizes Windows IIS logs (via nxlog or Blumira Agent)
There is nothing you need to do to enable these. These are rolling out to all of our customers now and will automatically begin watching for suspicious events.
Update – 1:16pm 2.21.24 – Through further research and review, it seems Sysmon should be able to catch some of this activity as well. Both previously mentioned 4663 events should generate sysmon event 11 (file create) events. If you used Poshim to deploy Blumira or use our Blumira Agent, you are already covered. While not recommended, you can also manually deploy and configure sysmon.
Update – 12:12pm 2.21.24 – Huntress has released a really great article getting into the details on these vulnerabilities and what to look for when exploited. Blumira is working quickly to build, test, and deploy these detections to our customers. Based off of Huntress’ research, the best indicators are based off of windows event ID 4663 and web server iis logs. If you don’t have these configured for your ScreenConnect web server, refer to these articles to help you do so:
- Event ID 4663 – How To Detect File Changes in Windows Server
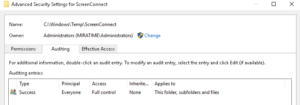
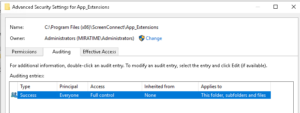
- After enabling 4663, you must set up a SACL on the ScreenConnect Directory at C:\Windows\Temp\ScreenConnect and C:\Program Files (x86)\ScreenConnect
- IIS Logging – Integrating with Microsoft Windows Internet Information Services
Update – 4:51pm 2.20.24 – PoC (Proof of Concept) exploit development is showing results with several researchers demonstrating exploitation in test environments. Successful exploitation results in a new ScreenConnect admin account being created. Monitoring for newly created users and login activity for your ScreenConnect instance is a good first step. Again, due to the nature of this vulnerability, no previous authentication is required, with Horizon3 stating the vulnerability to be “extremely trivial” to exploit. Reference – Horizon3 and Huntress
What Happened?
On February 19th, 2024, the IT Management Software company, ConnectWise, announced the identification of two vulnerabilities in their remote access tool, ScreenConnect. These vulnerabilities directly impact and target on-prem or self-hosted ScreenConnect Web Servers running version 23.9.7 and prior.
- CWE-288 Authentication bypass using an alternate path or channel
- CWE-22 Improper limitation of a pathname to a restricted directory (“path traversal”)
Due to the nature of these vulnerabilities, they have been assigned a critical severity by ConnectWise, defined as, “Vulnerabilities that could allow the ability to execute remote code or directly impact confidential data or critical systems.”
In regards to remediation and patching priority, ConnectWise has assigned this as high priority, “Vulnerabilities that are either being targeted or have higher risk of being targeted by exploits in the wild. Recommend installing updates as emergency changes or as soon as possible (e.g., within days)”.
These vulnerabilities were reported to ConnectWise on February 13th by an unnamed security researcher via the ConnectWise Trust Center. ConnectWise has stated that, “There is no evidence that these vulnerabilities have been exploited in the wild, but immediate action must be taken by on-premise partners to address these identified security risks.”
How Bad is This?
Vulnerabilities that lead to remote code execution are some of the most critical and severe issues out there and could lead to complete control over a targeted server. To make matters worse, ScreenConnect servers affected by these vulnerabilities are likely going to be public facing, making them easy targets for mass scans and exploitation.


What Should I Do?
Remediation
Cloud – For organizations using a managed ScreenConnect Cloud instance, no remediation action is necessary. “ScreenConnect servers hosted in ‘screenconnect.com’ cloud or ‘hostedrmm.com’ have been updated to remediate the issue.”
On-Premises/Self-hosted – Update ConnectWise ScreenConnect servers to version 23.9.8 immediately.
Investigation/Detection
Unfortunately, details are light at the moment and no indicators of attack have been publicly released. There has been no evidence of these vulnerabilities being exploited in the wild, but that is likely due to the age of this announcement and, as time goes on, will undoubtedly change as threat actors begin acquiring targets and weaponizing these vulnerabilities.
How Blumira Can Help
Blumira continues to actively monitor this issue, and look for ways that we can detect any stage of exploitation of these vulnerabilities. If Blumira gains the ability to detect the attacks using these vulnerabilities, it is most likely going to be via our endpoint agent. If you are running an on-prem ScreenConnect server, and you are already using a Blumira edition that supports endpoint agents, please ensure that you have the endpoint agent installed on your ScreenConnect server.
If you are an MSP and not already using Blumira, please submit a request for a “free for internal use” NFR account.
Blumira’s Free SIEM is easy to deploy; IT and security teams can start seeing immediate security value for their organizations.
Jake Ouellette
Jake is an Incident Detection Engineer at Blumira, where he contributes to research and design efforts to continuously improve the detection, analysis, and disruption capabilities of the Blumira platform.
More from the blog
View All Posts
Update Now: Microsoft Exchange Server Zero-Days
Read MoreVulnerabilities in Cleo Software Allow for Unauthenticated Remote Code Execution via CVE-2024-55956
Read More
Zero-Day Vulnerabilities Found in Microsoft Exchange (CVE-2022-41040 and CVE-2022-41082)
Read MoreSubscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.