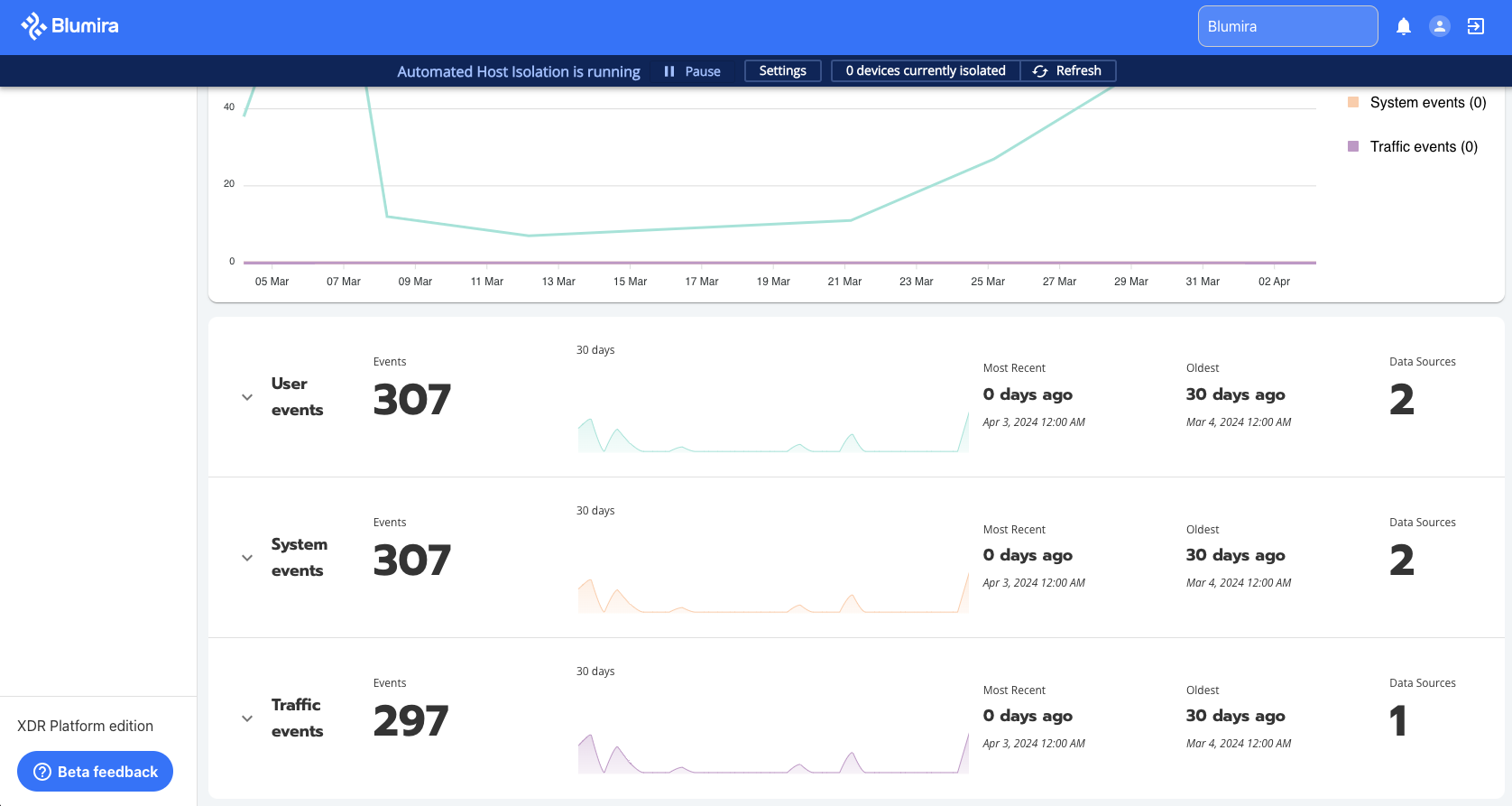
Quickly investigate security incidents by searching all logs in your environment
Blumira remains committed to providing usable solutions that help organizations strengthen their security posture and respond to incidents more effectively.
Our newest feature, Blumira Investigate, provides a holistic view of security events to accelerate investigations. By presenting this information in an intuitive dashboard, analysts can rapidly track threats, determine the full scope of an incident, and respond accordingly. Blumira Investigate enables IT teams to quickly identify patterns, anomalies, and potential threats, ultimately accelerating incident response times.
Key Benefits
- Comprehensive Data Correlation: Aggregates network traffic, user activity, system events, and other critical data sources into a unified dashboard to provide complete context around incidents.
- Intuitive Search and Filters: Enables analysts to easily investigate threats by quickly surfacing all events related to search terms. Save frequent searches and create reusable filters.
- Clear Visual Timelines: Graphically maps out associated events over time to reveal attack trends and scope to help analysts determine the full impact of an incident.
- Improved Efficiency: Consolidates all relevant information to eliminate the need for manual log review across multiple systems. Streamlines workflows to maximize productivity.
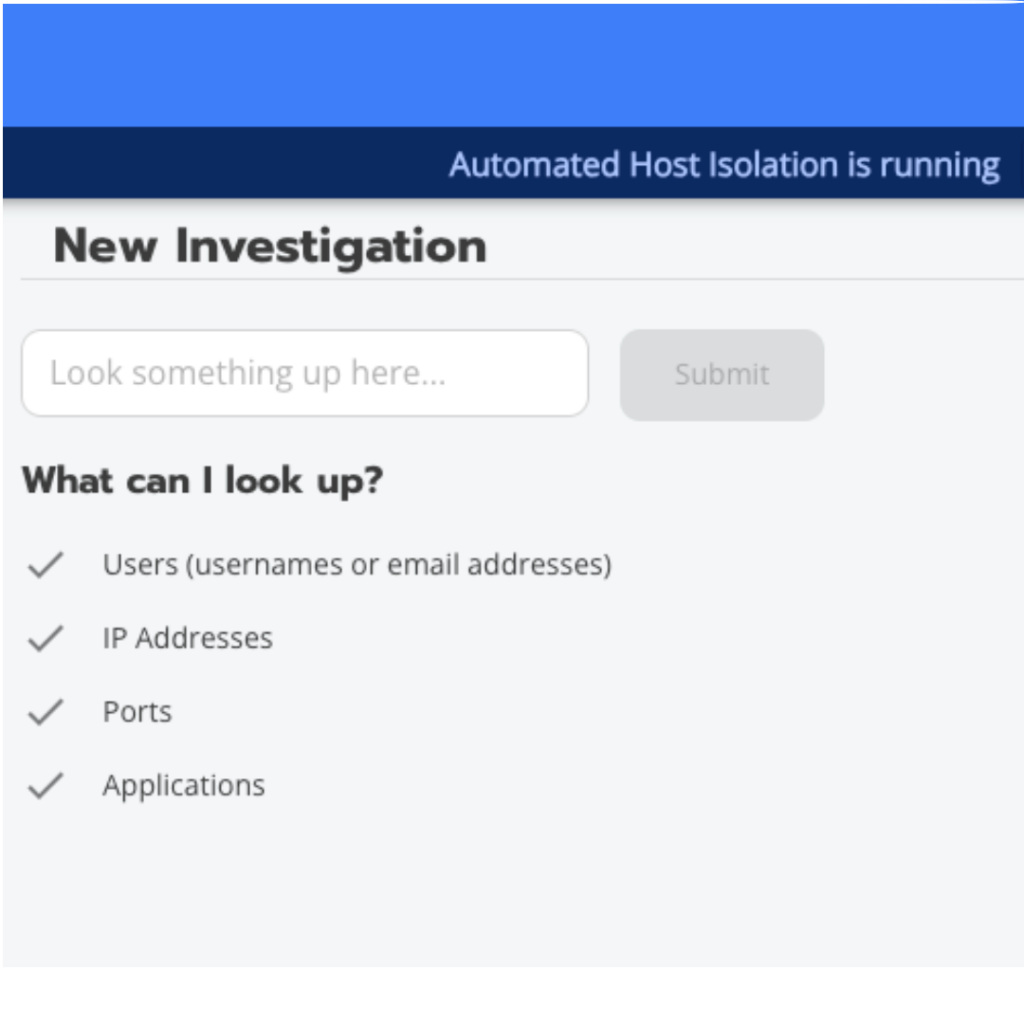
Use Cases
- Uncover Phishing Attacks: Imagine an employee reporting a suspicious phishing email that bypassed your security controls. Blumira Investigate allows you to search by the URL mentioned in the email. By analyzing DNS query logs, you can gain insights into the scope of the incident and identify potential risks.
- Assess Unusual Network Traffic Activity: Detecting an after-hours spike in network traffic to an external IP address over a specific port? Search by the port number to review network traffic logs. Blumira Investigate helps you pinpoint anomalies and assess their impact.
- Determine Impact of Malicious Processes: If a malicious process is observed running using a service account, searching by the username associated with that account reveals authentication logs. This information helps identify affected endpoints and take necessary action.
“I would love to say, ‘I want to see logs from this computer over the last 24 hours,’ because I think something might have been going on.” – CIO, Small Accounting Firm
Purpose-Built for Small and Medium-Sized Teams
Unlike large enterprises with extensive security staffing and complete SOCs, or small businesses that may tend to leverage MSPs, medium-sized companies often face a disproportionate security burden with limited resources.
Blumira Investigate empowers resource-constrained staff to slash incident response times through intuitive log search, integrated data correlation, and transparent visualizations.
By simplifying workflows, it allows analysts of all skill levels to hunt threats and enable precise response quickly. Specialized dashboards, historical graphs, and data correlation features provide the visibility needed to accelerate understanding of unfolding attacks.
Blumira Investigate automatically correlates relevant data across many different sources to surface meaningful insights into incidents. This means analysts spend less time manually piecing together data and more time acting on insights to protect the business.
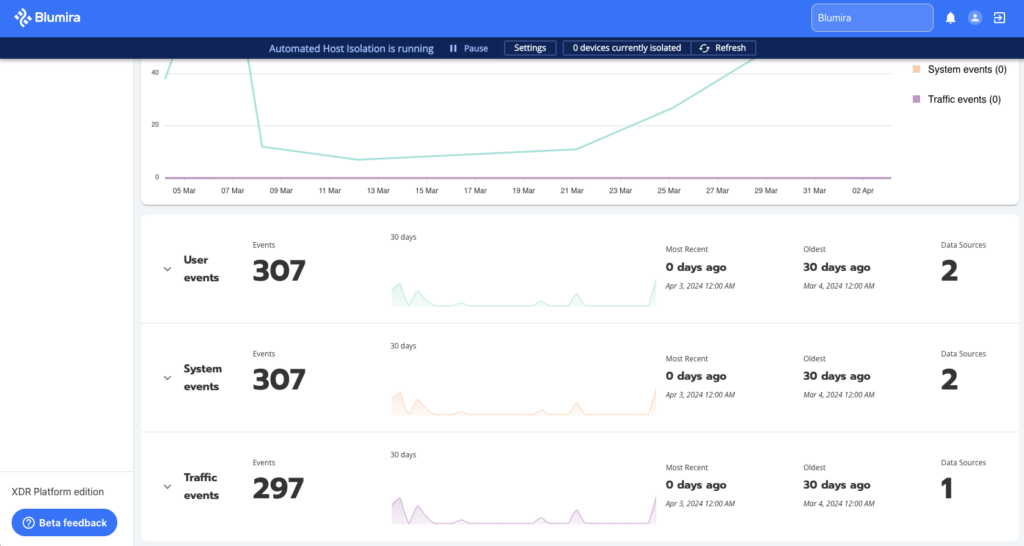
How to Get Started
- Log Search: Begin by searching your logs using parameters such as IP addresses, usernames, applications, or protocols. Blumira Investigate returns all related network traffic, users, systems, and applications.
- Quick Filters: Narrow down your search using quick filters, and customize your timeframes. Pinpoint the exact data you need without drowning in irrelevant information.
- Visualize and Act: Leverage the dashboard’s visualizations to gain insights. Armed with relevant data, your IT team can resolve issues faster and improve overall productivity.
Why Choose Blumira?
- Ease of Use: Blumira Investigate simplifies security tasks, allowing IT teams to focus on what matters most.
- Automated Response: Stop attacks in their tracks with automated response features. Guided playbooks ensure efficient incident handling.
- Forensic Investigation: Advanced reporting and dashboards facilitate forensic analysis, aiding in post-incident assessment.
- Flexibility: Blumira’s open, vendor-agnostic platform integrates seamlessly with other tools, providing flexibility within your budget.
Learn More About Blumira Investigate
For a video presentation on Investigate, watch Blumira co-founder and CTO Matt Warner, and product lead Brett Bzdafka roughly 12 minutes in. Blumira Investigate is included in Blumira SIEM+ and XDR solutions, available as of April 23, 2024. Read more. Experience simplified security firsthand with a free XDR trial account.

 Back to Blog
Back to Blog